The Internet of Medical Things (IoMT) is a network of medical devices that contain sensors and embedded software. These devices can connect to healthcare IT systems through the internet or other networks. IoMT is a fast-growing segment of IoT (Internet of Things) and is expected to grow into a $176 billion industry by 2026, according to Fortune Business Insights. However, this surge in popularity is accompanied by an increased focus on data security risks. According to a recent survey, 82% of healthcare organizations have experienced an IoT-focused cyberattack. This proves that it’s more important than ever to safeguard IoMT-generated data.
IoMT in Healthcare
The Internet of Medical Things has many applications in healthcare. The most well-known use-case is remote patient monitoring, with IoMT devices designed to monitor diabetes and other conditions, measure glucose levels and track heart rates, all while in a home setting. Other uses include devices that remind healthcare staff to sanitize their hands, connected inhalers that help asthma or COPD patients track their medication, and ingestible sensors that can collect data from inside the human body.
IoMT device manufacturers have developed ways to ensure that the device hardware is kept secure. However, it is equally, if not more, important to secure the data generated by these devices. In this article, we’ll describe how to keep data from IoMT devices secure and compliant with privacy regulations such as HIPAA.
Safeguarding IoMT Data: A Fictional Case Study
Let’s imagine that you’re developing an IoMT blood pressure monitor for consumer use. In our scenario, this device will come with a companion mobile app through which patients can configure their monitor, see their blood pressure charts, and share reports with their doctor or loved ones. We’ll also assume that all blood pressure readings and other patient data will be stored in the cloud so that they can be made available to patients at all times, and can be more easily shared with community health centers and electronic health records (EHRs).
When a patient buys one of our blood pressure monitors, they’ll first need to install the mobile app, pair their phone with the monitor using Bluetooth, and go through an initial secure registration workflow. The app will then share the patient’s home WiFi settings with the monitor so that it can access the internet autonomously whenever it needs to send a reading to the cloud.
One way to secure the data is to “silo” all sensitive Protected Health Information (PHI) in a secure and compliant platform, and avoid sharing sensitive patient information via a regular public IoMT network. Here’s how:
- When a patient installs and runs the companion mobile app for the first time, they are asked to register. Their registration data is sent from their phone to a secure API that stores it online. Since this data includes PHI, the API and database where it’s stored need to comply with regulations such as HIPAA. It’s therefore vital that the data is encrypted in transit and at rest, and that it’s stored on a compliant hosting provider.
- When the patient’s phone pairs with the monitor and shares the WiFi network information via Bluetooth, it also sends to the monitor a universally unique identifier (UUID) that identifies the patient. The blood pressure monitor stores this UUID in its memory.
- Whenever the patient takes a blood pressure reading, the monitor automatically uploads the data to the cloud. No PHI is transmitted at this time (just the UUID), so we can engineer our hardware to transmit the data via any public IoT network. Common IoT services include AWS IoT Core, Google IoT Core, and Azure IoT Hub. These services are also known as “MQTT broker services” because they provide publish/subscription (pub/sub) functionality using MQTT, a common IoT data protocol. This cloud-based service receives the data from the monitors and can perform some processing on it, such as storing it in a database or sending it to a custom application.
- To keep the blood pressure readings available for charting purposes, we’ll want to store them in a cloud database. Since the readings consist of a series of numbers and do not include PHI, they can be stored in a high-capacity online database such as Amazon DynamoDB or Azure Cosmos DB. Alternatively, they can be stored in the same database that hosts the PHI, which might be a good option if you want to “join” these readings with some of the data that the patient had submitted when they registered.
- Rounding out this solution is an “admin portal”, or a web-based administrative interface that allows you to manage the solution and provide support for patients. This connects to a secure database that stores all user account information, as well as PHI. Because of the presence of PHI, this part of the platform needs to be hosted on the compliant hosting platform.
Below is a diagram that illustrates this solution:
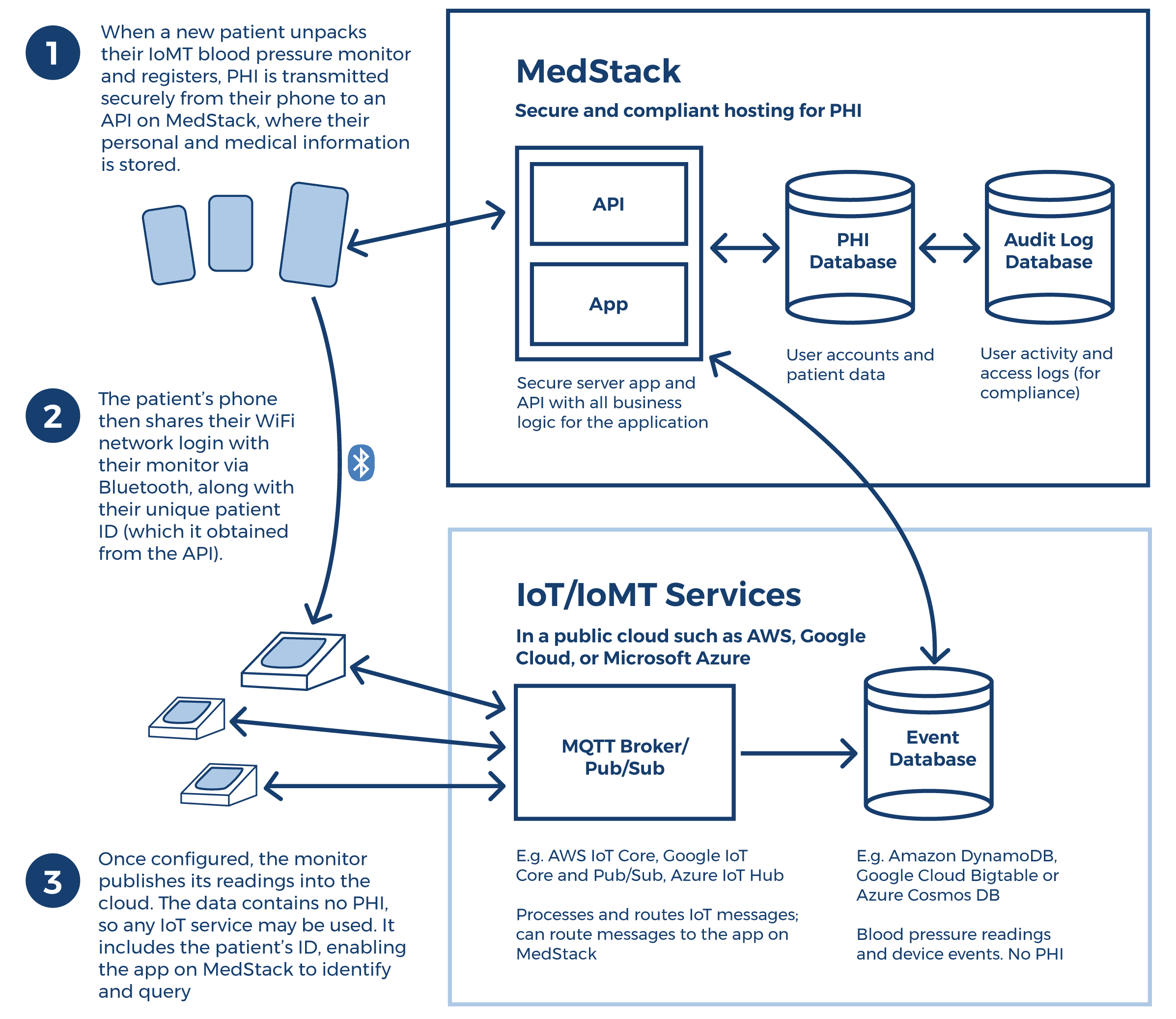
By giving our solution’s PHI a secure and compliant home, such as the one provided by MedStack’s platform, developing IoMT solutions that meet regulatory requirements is easy.
To learn more about how MedStack can help keep IoMT devices secure, book a demo today!
This post was written by guest blogger David Emerson. David runs SiteRocket Labs, a company that develops secure and engaging digital health applications.





