Due to increased data collection practices, individuals are more vulnerable than ever to having their information misused, with many feeling they have limited control over how their details are utilized.
As a response to mounting concerns, the European Union instituted the General Data Protection Regulation (GDPR) on May 25, 2018, to fortify data privacy and security for its citizens. Not only is GDPR the strictest data privacy law in the world, but it also has wide-reaching implications that extend beyond the EU’s borders.
GDPR is a European Union regulation that mandates how organizations—whether based in the EU or elsewhere—should handle and protect European citizens’ personal data.
This post aims to simplify personal data protection, providing a comprehensive GDPR compliance checklist that will steer you clear of potential pitfalls and ensure you’re on the right side of the law.
Understanding GDPR Basics
At its core, GDPR focuses on protecting personal data for all individuals within the European Union, creating a safer cyber environment.
GDPR is an all-encompassing regulation affecting a broad spectrum of organizations, ranging from large corporations to small businesses. It mandates that these entities adhere to a new standard of responsibility regarding customer data storage, sharing, and protection.
Key Definitions
- Data Subject: An individual whose personal data is collected, held, or processed.
- Personal Data: Any information relating to an identified or identifiable natural person (‘data subject’).
- Data Controller: The entity that determines the purposes and means of processing personal data on a lawful basis.
- Data Processor: An organization that processes data on behalf of the data controller.
- Data Processing: Any operation or set of operations performed on personal data, whether or not by automated means. This includes collection, recording, organization, structuring, storage, adaptation, retrieval, consultation, use, disclosure by transmission, dissemination, or otherwise making available, alignment, combination, restriction, erasure, or destruction.
- Consent: The data subject’s clear affirmative action signaling agreement to process their personal data.
- Data Protection Officer (DPO): An appointed individual within an organization responsible for overseeing data protection strategy and implementation to ensure compliance with GDPR requirements.
- Data Breach: A security incident where sensitive, protected, or confidential data is copied, transmitted, viewed, stolen, or used by an individual unauthorized to do so.
- Encryption: The process of converting data into a code to prevent unauthorized access.
The Seven Principles of GDPR
Here are the seven foundational principles of GDPR:
- Lawfulness, Fairness, and Transparency: Organizations must process personal data legally, fairly, and transparently. Each individual should be informed about how their data is used.
- Purpose Limitation: Personal data should only be collected for specified, explicit, and legitimate purposes. Organizations should only process it in a compatible manner.
- Data Minimization: Organizations should only collect the data necessary for the intended purpose, avoiding collecting excessive information.
- Accuracy: Personal data must be accurate and, where necessary, kept up to date. Organizations should take every reasonable step to ensure that inaccurate data is rectified or deleted without delay.
- Storage Limitation: Personal data should be kept in a form that permits identification of data subjects for no longer than is necessary for the purposes for which the personal data are processed.
- Integrity and Confidentiality: Organizations are required to process personal data in a manner that ensures appropriate security, including protection against unauthorized or unlawful processing, accidental loss, destruction, or damage, using appropriate technical or organizational measures.
- Accountability: The accountability principle requires that organizations take responsibility for the personal data they hold and can demonstrate compliance with the other principles, implementing necessary policies, procedures, and measures.
Start With Data Inventory and Mapping
Before diving into GDPR compliance, it’s crucial to understand how data is processed and held within your organization. This involves creating a comprehensive data inventory, understanding its flow, and developing proper documentation.
- What kind of personal data are you collecting?
- Who has access to this data?
- Why are you collecting this personal data?
- Where is the collected personal data stored?
- Is sensitive personal information safe?
- How do you request and record consent, especially for kids under 16?
- Are all departments documenting how they use the personal data?
- Is someone in each department overseeing how data is used?
- Can you track where data goes from when it’s collected till its deletion?
- Do you have rules for how third parties should handle the data you share with them?
- How do you decide how long to keep data, and how do you safely eliminate it?
Your Records of Processing Activities (ROPA) should document the categories of data being processed, the legal grounds for such actions, the purpose of processing, and how long this data is retained.
Create a data flow map to know how personal data travels and is stored within your company.
Think of it as a guide that showcases the journey of data, from the moment it enters your system through various departments until its deletion. It helps you closely monitor data handling, ensuring secure transfers and safe storage points.
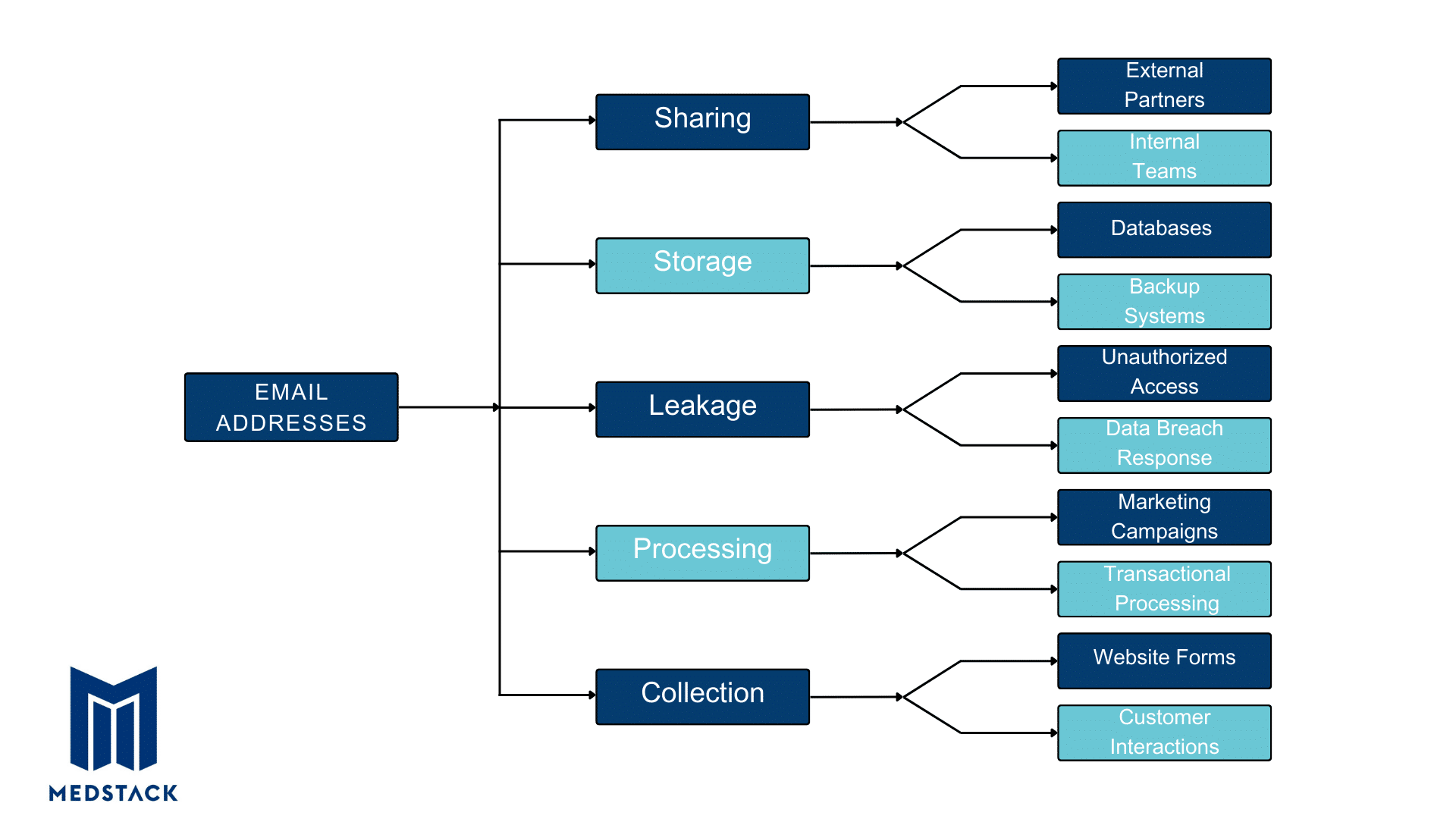
Obtain Consent For Lawful Processing
Obtaining consent is more than just having a privacy policy on your website; it’s about safeguarding your users’ rights to privacy and data protection.
When asking for consent about data collection and processing, it should be:
- Freely Given: The users should have a choice without any pressure or consequences of refusing. For instance, you can’t hide consent in terms and conditions or force users to consent to unnecessary data collection to use your service.
- Specific: The consent request must be clear and distinguishable from other matters, providing sufficient information for users to make an informed decision.
- Informed: You must provide users with all the essential information regarding data processing, including the purpose, types of data collected, and their rights, including the right to withdraw consent at any time.
- Unambiguous: Consent from users should be obtained through clear affirmative action and plain language, avoiding pre-ticked boxes or implied consent through inactivity.
Sometimes, you’ll need ‘explicit consent,’ which requires a more direct confirmation from the user. This might be a signed document, an electronic form, an email, or a verified two-step authentication process.
If your existing consent protocols don’t meet GDPR guidelines, it’s time to revise. ‘Re-consent’ users with the new, lawful protocols in place.
A Comprehensive Privacy Policy
A well-documented privacy policy is a legal obligation that aligns with the GDPR guidelines, clearly outlining:
- Who controls the data?
- What kind of data are you collecting, and the reasons behind the data collection?
- How is the data collected and processed?
- Who has access to this data, including any third-party service providers?
- The geographical areas where the data might be transferred?
- How long is the data stored?
- Instructions on how users can exercise their data rights?
Understand Data Subject Rights
Here’s a list of the key data subject rights according to GDPR:
- Right to Access: Individuals can request access to their personal data and ask how it is used by the company after it has been gathered. Organizations must respond to such requests within 30 days (Article 15).
- Right to Rectification: If the personal data collected is incorrect or incomplete, users have the right to have the errors corrected (Article 16).
- Right to Erasure (or ‘Right to be Forgotten’): Users can request to stop their data processing and its deletion (Article 17).
- Right to Restrict Processing: Individuals have the right to block or suppress the processing of their personal data on a legal basis (Article 18).
- Right to be Informed: Users have the right to know how their data is being used, rectified, or erased. Your privacy policy should clearly detail the data processing activities (Article 19).
- Right to Data Portability: This allows individuals to retain and reuse their personal data for their own purposes (Article 20).
- Right to Object: Users can object if the organization rejects a request to stop their data processing, according to Article 18 (Article 21).
- Rights Related to Automated Decision-Making and Profiling: Individuals have the right not to be subjected to a decision based solely on automated processing, including profiling (Article 22).
Developing an Efficient Plan for Handling SARs
To respect these rights effectively, your business should have a robust mechanism to handle Subject Access Requests (SARs). Here is a guide to help you develop a reliable plan:
- Quick Response Time: You must respond to SARs within 30 days of receiving the request (Previous allowed time was 40-days).
- No Fee for Compliance: Typically, you must not charge a fee for complying with a request unless it is clearly baseless or excessive.
- Refusing Unreasonable Requests: You have the right to refuse requests that are groundless or excessive, but in such cases, you need to clearly communicate the refusal reason to the individual, informing them of their right to complain to the supervisory authority or seek legal services, all within a month.
- System Preparedness: Assess if your current systems can manage a high volume of SARs, including providing additional information like data retention periods and rectifying inaccuracies.
Appoint a Data Protection Officer (DPO)
Setting up safeguards for user data is a big deal, and having a Data Protection Officer (DPO) can play a huge role in that. However, not every company needs to appoint a DPO.

It really depends on what your company does and how it handles data. Typically, you’d need to consider getting a DPO onboard or data protection authority if:
- Your enterprise operates as a public authority.
- Your core operations entail the regular and systematic monitoring of individuals on a large scale.
- Your company engages in the processing of special categories of data, such as health records or details about criminal convictions and offenses, also on a significant scale.
Even if your business doesn’t check these boxes, having a DPO can still be a good move. It’s a proactive way to show your customers that you take data protection seriously, aligning with the best practices suggested by industry groups like the Article 29 Working Party.
Prepare Your Teams for Data Breach and Incident Response
When it comes to data breaches, being prepared is half the battle. Here’s a straightforward breakdown to set your teams on the right path:
- Documentation: Always have a current record of your data processing activities.
- Securing the Site: Restrict access to your website until the vulnerability is resolved.
- Deep Dive: Investigate every aspect of the breach — pinpointing the how, when, and where. Figure out the data affected and the users impacted.
- Report It: According to Article 33, Within 72 hours, inform the appropriate supervisory authority, detailing the breach scope, affected data, and the probable impact.
- Reach Out: If there’s a high risk for your users due to the breach, notify them and advise protective measures.
- Review and Revise: Update your site’s protection policies and security measures to prevent future breaches.
- Future Prep: Design a strategic plan to handle potential breaches in the future.
Conduct Data Protection Impact Assessments (DPIAs)
A Data Protection Impact Assessment (DPIA) is an organization’s systematic process to identify and minimize the potential privacy risks associated with handling personal data.
To do a proper DPIA, you can use the template provided by GDPR guidelines. And remember, always loop in your data protection officer while doing a DPIA, as advised in GDPR’s Article 35.
When Do You Need a DPIA?
You need to do a DPIA under several circumstances, like:
- If you’re using new technology.
- If you’re tracking people’s location and behavior.
- If you’re watching public spaces on a big scale.
- If you’re dealing with sensitive info like race, religious beliefs, health details, sexual orientation, or data about a person’s private life.
- If using the data to make automatic choices about people, that might have serious effects.
- If you’re handling children’s data.
- If the data (if leaked) can cause physical harm to people.
How to Do a DPIA According to GDPR Guidelines
Article 35 of GDPR lays out what you need to include in a DPIA, such as:
- A clear explanation of the planned data usage activities and why they are being done, including any legit reasons backed by the controller.
- A critical look at the need and balance of these activities concerning their objectives.
- A detailed check of the protection risks to people’s rights and privacy.
- The planned steps to tackle these risks include safety nets, security actions, and ways to protect personal data and comply with GDPR, considering the rights and true interests of the individuals and others involved.
Review and Monitor Continuously
To stay on top of GDPR, you must check how your business follows the rules regularly. Think of it like a regular health check-up but for the privacy of your user data.
Just like technology, regulations can change over time. Keep a finger on the pulse of any updates or changes in GDPR rules to monitor these shifts. You should adjust your business protection processes swiftly, keep up with the latest requirements, and not be caught off guard.
To prove that you’re doing your part in protecting user data, conducting internal audits and maintaining detailed records of your compliance efforts is key.
This not only helps showcase your dedication towards data protection but also comes in handy in any regulatory scrutiny.
Final Thoughts
Achieving GDPR compliance varies based on your organization’s specifics and the data you are handling. Luckily, there are many resources available to assist. Ready to position your business as a leader in data security? MedStack has your back. Our experts are here to simplify GDPR compliance for you, offering tailored strategies that align with your business objectives.
So, why wait? Dive in and secure a prosperous, data-protected future with MedStack.