Some day, every digital health company is going to do an audit. And that auditor is going to ask for a list of all of your suppliers, their systems, and who has access. Along with proof that you are reviewing access every three months.
Vendor management and access control are two critical aspects of HIPAA compliance, both touching on elements of the technical and administrative safeguards that fall outside of the responsibility of major cloud providers.
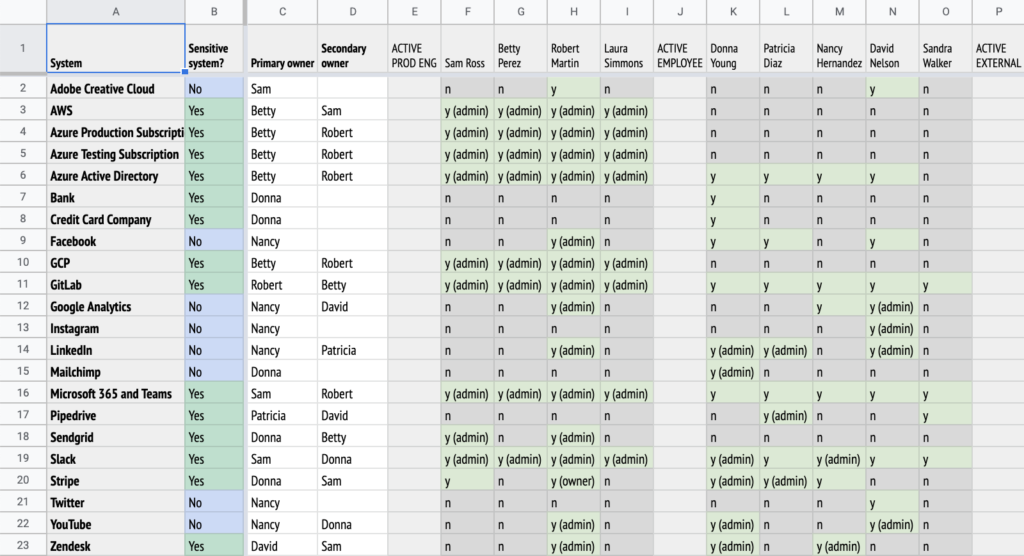
What to do? We’ve built a handy spreadsheet that you can use to track all of these things and more, to make your life easier come audit time.
One tool, many uses
This spreadsheet is good for more than access tracking. It’s based on an actual spreadsheet we use internally, and here’s what it can do:
Track all of your suppliers and vendors. I don’t know about you, but MedStack has over 70 suppliers with web apps that we log into. There’s so many useful SaaS tools out there, and we don’t want to stifle the innovation of our employees in adopting useful tools. So we track them carefully and make sure that each tool has a champion who owns the system and handles any issues that come up. They also create an admin account for our compliance officer so that we can review access every quarter.
Remove access from every system when someone leaves. At any company, people come and go from time to time. When someone leaves, it’s important to immediately remove their access from each system. This is just common sense and good practice. With this spreadsheet, we know what they had access to and we know who can administer that system to remove their access.
Manage multiple admins for each system. It’s Saturday night and you need a critical update to a system — but your only admin is paddleboarding in the Arctic, or base jumping off Angel Falls. Oops—should have had another admin on the system. With the spreadsheet, you can check that you have at least two for every system.
Save money. The first time you do a full access review on all of your systems, you’re going to make a good friend in your COO. They will be very happy as you delete unused accounts and cut your SaaS bills. You might even find systems that no-one is using any more.
What do the rules have to say?
When you go into an audit or an assessment, you will be benchmarked against a set of rules. Here are some of the most critical for digital healthcare:
| HIPAA | US law | Governs the handling of protected health information |
| ISO 27001 | International standard | Provides a framework for information security management |
| SOC 2 | Industry standard | Auditing framework for how service providers manage data |
HIPAA
HIPAA is the grandparent of health data protection laws throughout the world, so let’s have a look at what it requires for access control.
Here are some quotes directly from the law. This template will help you to implement the parts in italics.
| HIPAA Administrative Safeguards
45 CFR § 164.308(a)(4)(i) |
(i) Standard: Information access management. Implement policies and procedures for authorizing access to electronic protected health information that are consistent with the applicable requirements of subpart E of this part. |
| HIPAA Administrative Safeguards
45 CFR § 164.308(a)(4)(ii)(B) |
(B) Access authorization (Addressable). Implement policies and procedures for granting access to electronic protected health information, for example, through access to a workstation, transaction, program, process, or other mechanism. |
| HIPAA Administrative Safeguards
45 CFR § 164.308(a)(4)(ii)(C) |
(C) Access establishment and modification (Addressable). Implement policies and procedures that, based upon the covered entity’s or the business associate’s access authorization policies, establish, document, review, and modify a user’s right of access to a workstation, transaction, program, or process. |
| HIPAA’s Technical Safeguards
45 CFR § 164.312(a)(1) |
(1) Standard: Access control. Implement technical policies and procedures for electronic information systems that maintain electronic protected health information to allow access only to those persons or software programs that have been granted access rights as specified in § 164.308(a)(4). |
| HIPAA’s Technical Safeguards
45 CFR § 164.312(a)(2)(i) |
(i) Unique user identification (Required). Assign a unique name and/or number for identifying and tracking user identity. |
ISO 27001
ISO 27001 is a great international framework for cybersecurity. It has strongly influenced a number of other cybersecurity frameworks and has the advantage of being well organized and easy to understand. These are some of the ISO controls that this template will help to implement.
| ISO 27001 A.9.1 Business requirements of access control |
Objective: To limit access to information and information processing facilities. |
| ISO 27001 A.9.2 User access management |
Objective: To ensure authorized user access and to prevent unauthorized access to systems and services. |
| ISO 27001 A.9.2.5 Review of user access rights |
Asset owners should review users’ access rights at regular intervals. |
| ISO 27001 A.9.4 System and application access control |
Objective: To prevent unauthorized access to systems and applications. |
SOC 2
SOC 2 has a set of Criteria which this template can help to achieve.
| SOC 2 Common Criteria 6 |
Logical and Physical Access Controls |
| SOC 2 Common Criteria 6.2 |
Prior to issuing system credentials and granting system access, the entity registers and authorizes new internal and external users whose access is administered by the entity. For those users whose access is administered by the entity, user system credentials are removed when user access is no longer authorized. |
| SOC 2 Common Criteria 6.2 excerpt |
Reviews Appropriateness of Access Credentials — The appropriateness of access credentials is reviewed on a periodic basis for unnecessary and inappropriate individuals with credentials. |
What does our template cover?
The template we’ve developed is a swiss-army knife for compliance, addressing whole sections of the frameworks and regulations above. It covers:
- Systems. The SaaS/PaaS/IaaS tools we use, our vendors and suppliers.
- Owners. The primary and secondary owners for each system. These are the go-to contacts for anything that our employees need changed.
- Each person and their access. This shows who has access to each system, and we divide it into sections. First, the production engineers who typically have administrative access to all of the critical systems. Then come regular employees and external contractors, as well as API access. Finally are removed users in a group that you can show and hide.
- User count. Useful to do a sanity check and see which systems are heavily used.
- Extra authentication information. Have we enabled 2FA/MFA or SSO (in the rare case it’s not super expensive).
Also covered is security and confidentiality risk information:
- Risk assessment. This is a simple risk check where we mark a “Yes” if the system is used for production data, receives PHI or credentials, has data that could help an attacker, or has financial data. It feeds into column B, which shows “Yes” if any of those are true — meaning this is a sensitive system that needs extra care.
- Description. A simple one-liner so our auditors know what each system does.
- Security info. We gather a complete set of security documentation for each of the most critical suppliers. We download or print to PDF all of the web pages and files. Here are links to the supplier’s legal agreements, certifications, security page, and what security functions they handle for us.
The other tabs:
- Owner counts. To see if ownership is relatively even spread across our employees.
- Update log. Last but not least, we have a written log of major updates and changes.
The version history:
- Audit log of changes. In order to prove we are keeping it up to date, we also use the automatic version history built into the spreadsheet (a feature of Google Sheets and Office 365).
Special features
I occasionally run an internal class on spreadsheet-fu, and there’s a number of features in this sheet that make it easier to use.
- Conditional formatting. We want to easily see who has access, so conditional format rules are set up to mark cells that start with “y” to green, and cells with “no” as gray. For the analysis parts of the spreadsheet, “Yes” is green and “No” is blue (avoid red, as it’s tough to read against green for people who are colour blind).
- Colour scale. This is handy for comparing numeric values. The “number of users” section gets darker green when more users have access to an app.
- Narrow font. I use the free font PT Sans Narrow, which makes it easier to fit more columns on to one screen, just like in old phone books.
- Formulas. the “Sensitive system?” column uses a COUNTIF formula to show that a system is considered sensitive from a security point of view. It just checks if any of the four criteria in columns AD-AG are true.
- Pivot table. These are a bit tricky to use — the second tab has a relatively straightforward pivot table to check to see if anyone is overloaded in how many systems they own.
How to do an Access Review
One of the requirements of SOC 2 (and other frameworks) is a quarterly review of every single user on every single system to make sure they are correct. It’s a worthwhile activity: no matter how carefully we manage our user access, there’s always a few changes that need to be made.
- Clear your schedule for a whole day, or more, depending on:
- How many systems you have
- How many employees you have
- How up-to-date your spreadsheet already is
- Find the page on the system that shows all of the users.
- Once you find it, copy the link into the spreadsheet, apply it as a link on the supplier’s name in column A.
- Make a screenshot.
- Zoom out in your browser window until the whole list is visible in one screenshot.
- You could also Print or Export the page to PDF, but we have found auditors prefer screenshots.
- Rename the screenshot to add the name of the vendor to the beginning of the name.
- Put the screenshot in an access review evidence folder. You’ll zip that later and send it to your assessors.
- Reconcile the screenshot to the access that’s listed in your spreadsheet.
- When you find differences, either fix them on the system, or fix the spreadsheet.
- Update the log, and celebrate with your co-workers.
Ready to give it a try? Get the template here.