We’re excited to introduce our new podcast, where we explore topics that are most relevant to our industry and business. Our first episodes features a discussion on GDPR and healthcare technology. Take a listen and read our show notes below!
Crystal, MedStack’s Communications Manager, and I had a chance to sit down a few weeks ago to chat about GDPR. This famous (in certain circles) regulation is the most individual-friendly piece of privacy legislation the internet has ever seen. But how does it mix and interact with healthcare data laws like HIPAA? Together we revisited a presentation that I made to the Toronto CTO meetup that covered just that question.
We also asked more questions: What is GDPR? How does it compare to HIPAA? Why is it so hard to implement?
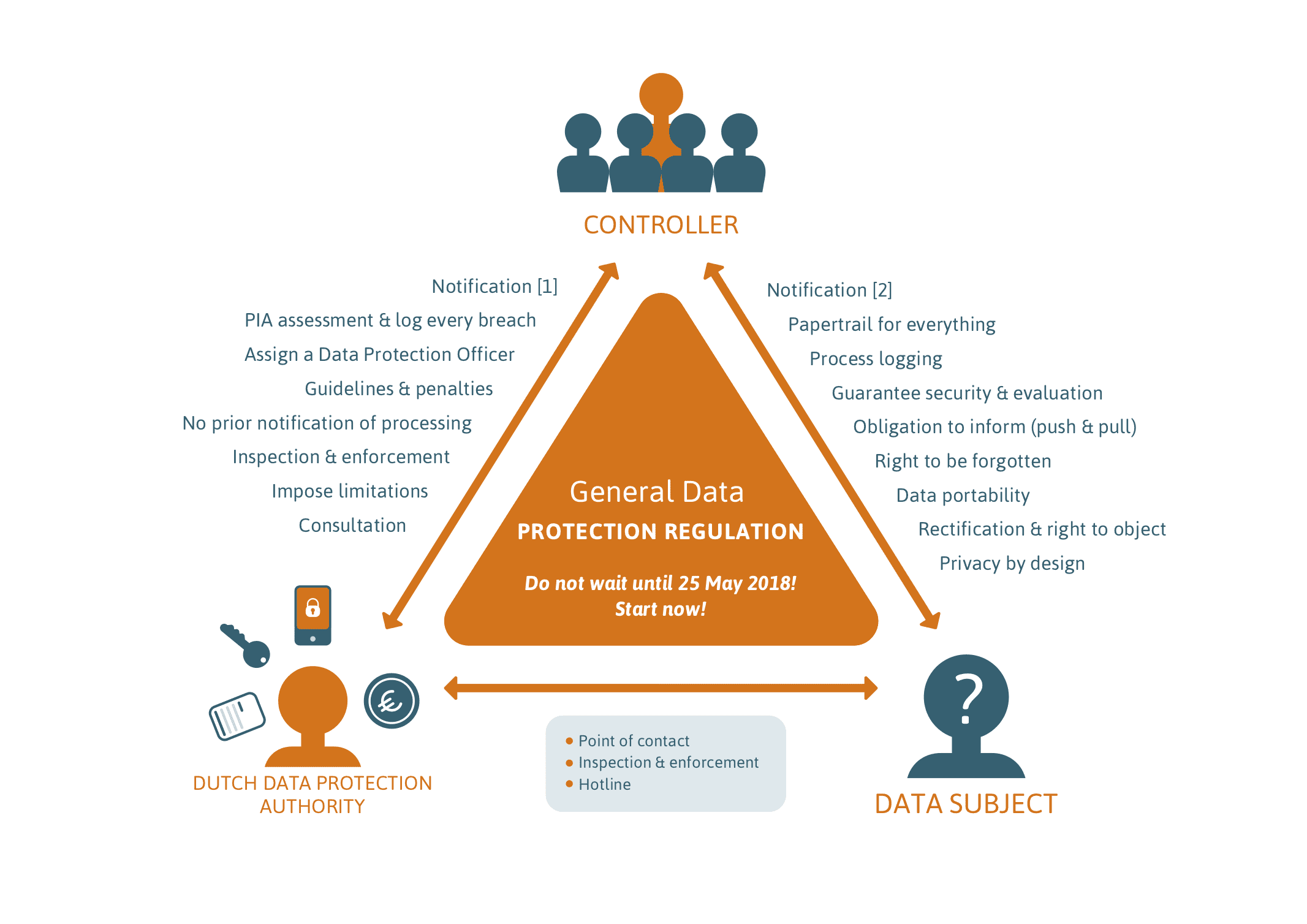
First, we ran through a background on GDPR, which gives a number of superpowers to individuals like the right to be forgotten, which may make your data architect nervous. Next, we did a quick background on the US HIPAA law on health data, and the equivalent laws in Canada, which require administrative, physical and technical safeguards. General privacy and health data privacy laws overlap, with the stronger rules generally taking precedence.
“We’re not googling anything!”
One reason why GDPR has triggered a massive onslaught of privacy policy updates, is that the fines can be very high (how high? Listen to the podcast!). HIPAA fines regularly hit the millions of dollars.
Comparing GDPR and HIPAA, we also talked about how long you have to report a breach, how detailed they make their technical requirements, and what they say about consent, and the philosophy of writing legislation.
“Be aiming to read the entirety of the laws that affect you.”
Lastly, Crystal asked me about why it’s so challenging for tech teams to implement to these standards. A big factor is that much of the software and infrastructure that software developers use is insecure by design. For example, out of the box the encryption is turned off, if it’s available at all. How did we wind up with Node.js tutorials that encourage plaintext password storage?
I suggested that a key question to ask yourself and your team is: what would happen if someone reported a security hole? This is primarily an issue of culture where the leadership comes from the top. Would they be criticized or thanked? How could you get to where you are, to supporting a healthy security bug bounty program?
We wrapped up our podcast there, and we definitely plan to make more in the future.