Imagine this: you’re a medical transcription company. Your customers want easier access to their transcript files so you set up a web portal. You build or buy a system that’s easy to use and does the job.
Then one day you wake up and find out that you’ve got 60 days to report a breach.
What went wrong? Earlier this week KrebsOnSecurity reported that MEDantex leaked 2700 doctor’s transcripts. They were also hit by a ransomware attack, which means it’s pretty certain that the records are now being sold on the deep web black market. I verified that the breach was genuine using Google’s Web Cache, which archives publicly accessible websites. I found myself looking at documents like “Operative Report”, a description of an operation on an abdominal aortic aneurysm, complete with name, date of birth, record numbers, diagnoses, and procedures.
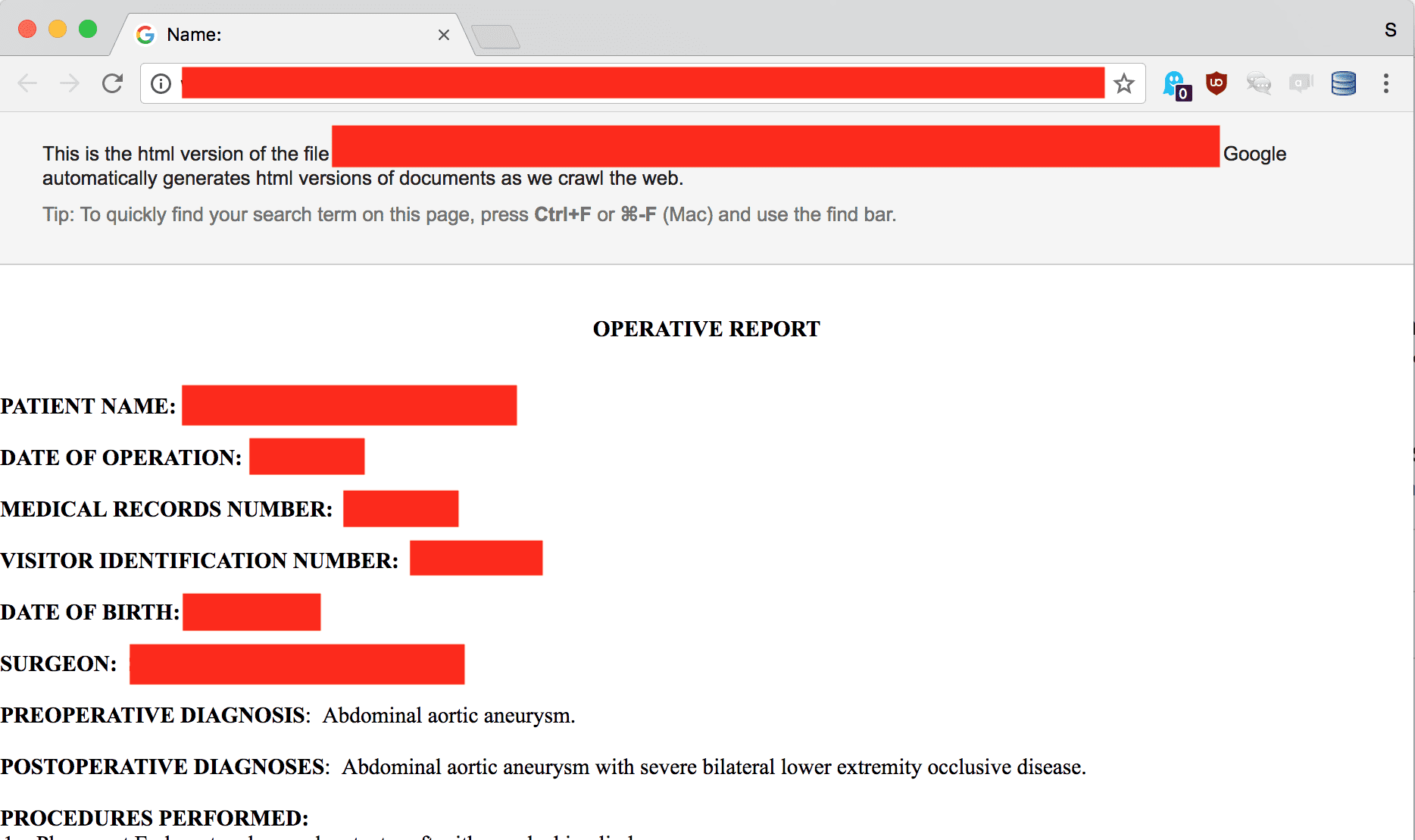
This is not the kind of information you want out there. You could be subject to blackmail, identity theft for financial gain, or someone could impersonate you in order to use your health insurance to get free medical procedures. In the process they might corrupt your medical and insurance records leading to consequences for you down the road.
MEDantex talks the talk when it comes to HIPAA compliance. Their website says:
“MEDantex is serious about keeping your data secure. We are HIPAA-compliant and our servers are protected with 128-bit encryption. Our security and HIPAA compliance team is made up of department managers and headed by a security officer that continually monitors your data.”
And they mention that they have “Secure web portal logins”. But in fact, their portal was not protected by any access control at all.
Let’s ask HIPAA what went wrong here. It says that you must:
“implement technical policies and procedures […] to allow access only to those persons or software programs that have been granted access rights.”
Pretty straightforward, right? You didn’t do that? Perhaps you should have hired a third party security company to do an assessment on your web app. HIPAA says:
“Implement policies and procedures to prevent, detect, contain, and correct security violations.”
ISO 27001 gets a little more specific, saying that you need an
“independent review of information security” at “planned intervals or when significant changes occur”.
Any competent expert would find a web portal that has no login.
Now you’ve got a breach on your hands, and you have 60 days to inform the government. In fact, what you need to do is notify each and every one of the doctors, clinics, and hospitals that were using your service. They need to:
- Notify each of the individual patients affected (so, maybe ten thousand or more patients).
- Announce the breach publicly on your website or in an ad to reach people who you can’t contact directly.
- Notify the major media.
- Notify the Health and Human Services Secretary.
Guess what clinics and hospitals don’t like? Being on the front page because they had a breach. It makes them look bad, it makes their patients not like them and go to other hospitals and clinics and sue them. They are going to pass the pain on to you. For example, they will probably look for another transcription service that has better security and doesn’t have breaches.
Now that you’ve dealt with all of that pain, you can expect one final consequence—a government audit. They’re going to come in and (a) examine everything about this breach and (b) dig for other privacy and security problems in your organization (and maybe at the hospitals and clinics that were using your service). They will fine you from $100 to $50,000 per violation or per record lost. The US Department of Health and Human Services maintains a public list of current large investigations (almost 400) and a larger list of past investigations (almost 2000). In the case of MEDantex we know there were about 2700 professionals involved, so let’s say ten thousand records. That’s pretty much going to hit the maximum fine of $1.5 million.
But wait, if they find more violations of other rules when they audit you, they can fine you separately for those. And just wait until the GDPR kicks in—instead of 60 days to notify, you get three days, and the maximum fine is 4% of your company’s global cash turnover. That could be in the billions of dollars for some large companies.
If the fines are so bad, why does this keep happening?
The open secret of the software industry is: there’s a lot of bad software out there. The consequence in healthcare is a lot of data breaches. This was a fairly small one, which sort of makes it easier to grok. To get an idea of the true scale of the problem:
- Protenus reported in 2017 that there were 27 million medical records breached in 2016.
- Banner Health in 2016 lost 3.7 million records and is facing a major investigation and a class-action lawsuit from their patients. Their food and beverage outlets were insecure.
- Middletown Medical recently lost records for 63,551 patients, because a database port was left open.
And so on, and so on. MEDantex and all of these cases show us how not to do healthcare security. To return to the original question, we have gone through a lot of measures that could have easily prevented a breach like this one. It’s reasonable to assume that many of those measures, and many others, weren’t followed by this company. So if you’re ever wondering why you need to care about compliance, here’s a great example.





