MedStack’s security posture has been reviewed and accepted in implementation by healthcare enterprises, government agencies and academic institutions, including North America’s most notable payers and providers.

At MedStack, security and privacy are baked into our platform from the start. Each of our implementations is mapped to HIPAA, SOC 2, ISO 27001 and other compliance frameworks that allow applications running on MedStack Control to inherit our platform’s provable privacy and security guarantees.

MedStack’s team of infrastructure, compliance, and security experts actively manage all environments running on MedStack Control, including upgrading operating systems, runtime orchestration, handling software end-of-life, intrusion detection, threat mitigation, evidence generation and more.
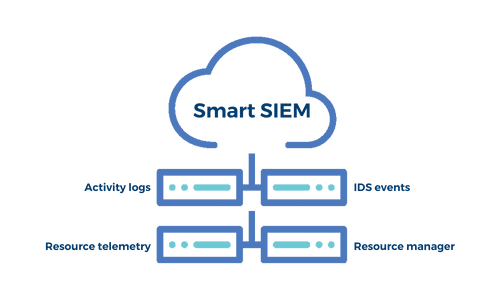
MedStack’s SIEM (Security Information and Event Management) works alongside our Intrusion Detection System (IDS), File Integrity Monitoring (FIM) and MedStack’s on-call engineer alerting tools by ingesting log sources. MedStack logs and event monitoring data are segmented by customer.
Our SIEM is under 24/7 intrusion detection system monitoring by designated on-call production engineers. Critical IDS/FIM event alerts are actively triaged by a 24/7 SOC team. If the activity looks abnormal, our team will contact you to help them investigate further.


MedStack undergoes annual audits and works with third-party vendors to maintain our security and compliance posture, including annual third-party penetration testing by qualified assessors.
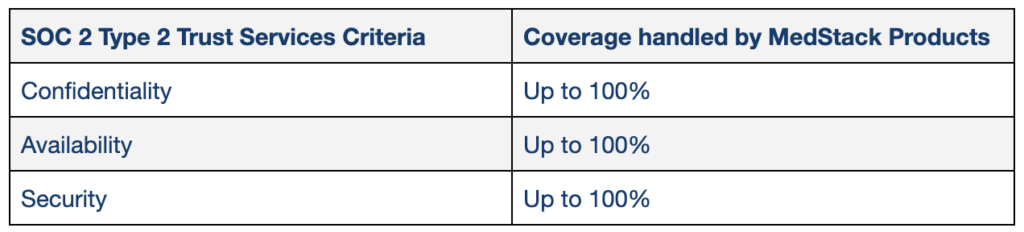
MedStack’s SOC 2 report can serve as evidence for up to 60% of SOC 2 Trust Services Criteria during your SOC 2 audit process. There are no other platforms that currently exist that can pass through such vast amounts of evidence as a benefit to its digital health users.
We work with an independent auditor to maintain our SOC 2 Type 2 report. MedStack’s SOC 2 report can be provided to your auditor as evidence, validating proof for three of the different SOC 2 Trust Services Criteria.


Our Privacy Impact Assessments (PIA) and Threat Risk Assessments (TRA) are done regularly by third parties. We use these to spot potential weaknesses and help prevent, or reduce, harmful outcomes.

Everything you need to know about SOC 2 for healthcare startups and how to prepare for a successful SOC 2 audit.

Book a demo today and see how easy it is to get started with MedStack.
About
Our Platform
MedStack Control
Exos by MedStack
Blog
Resources
Documentation
MedStack Control
Exos by MedStack
Legal
Learn how MedStack can help you.