While most technical teams know that data security and privacy compliance are crucial for the success of any digital health company, few actually anticipate the required effort, prioritize developer time, and have the internal knowledge that’s required to build and maintain these systems.
Maintaining compliance in regulated markets is not a “set it and forget it” task. It’s an ongoing effort that is often underestimated. In healthcare, it can take several months to build and implement the long list of required HIPAA controls, causing teams to divert focus away from application development and system design.
At MedStack, security and privacy are baked into our products from the start.
We’ve implemented compliance controls as code, designing deliberate privacy and security requirements into infrastructure that provisions single-tenant cloud resources to power and protect application environments. Each implementation is mapped to HIPAA, SOC 2, ISO27001 and other compliance frameworks that allow applications running on MedStack Control to inherit our platform’s provable privacy and security guarantees.
For managing the ongoing maintenance activities like upgrading operating systems, runtime orchestration, handling software end-of-life, intrusion detection response, threat mitigation, evidence generation and more, MedStack’s team of infrastructure, compliance, and security experts actively manage all environments running on MedStack Control.
By simply deploying applications to MedStack Control, teams inherit up to 75% of all administrative, technical, and physical HIPAA controls. This can save months of upfront work and hundreds of hours each year on privacy and security work that would otherwise have to be owned entirely in-house.
On this page, we have compiled an overview of MedStack’s Security Program that backs some of the most prominent digital health companies in North America and Europe.
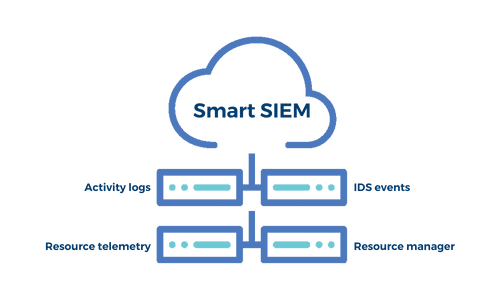
MedStack’s SIEM (Security Information and Event Management) works alongside our Intrusion Detection System (IDS), File Integrity Monitoring (FIM) and MedStack’s on-call engineer alerting tools by ingesting log sources. MedStack logs and event monitoring data are segmented by customer.
Our SIEM is under 24/7 intrusion detection system monitoring by designated on-call production engineers. Critical IDS/FIM event alerts are actively triaged by a 24/7 SOC team. If activity looks abnormal, our team will contact you to help them investigate further.
MedStack undergoes annual audits and works with third-party vendors to maintain our security and compliance posture.
MedStack’s SOC 2 report can serve as evidence for up to 60% of SOC 2 Trust Services Criteria during your SOC 2 audit process. There are no other platforms that currently exist that can pass through such vast amounts of evidence as a benefit to its digital health users.
We work with an independent auditor to maintain our SOC 2 Type 2 report. MedStack’s SOC 2 report can be provided to your auditor as evidence, validating proof for three of the different SOC 2 Trust Services Criteria.
SOC 2 Type 2 Trust Services Criteria | Coverage Handled by MedStack Products |
Confidentiality | Up to 100% |
Availability | Up to 100% |
Security | Up to 100% |
Privacy | 0% |
Processing integrity | 0% |
We complete annual third-party penetration testing by qualified assessors.
Our Privacy Impact Assessments (PIA) and Threat Risk Assessments (TRA) are done regularly by third parties. We use these to spot potential weaknesses and help prevent, or reduce, harmful outcomes.
Our user activity log allows our customers to see who did what, and when.
MedStack’s network-based application firewalls allow you to detect unwanted applications or services using a non standard port, or detect if an allowed protocol is being abused. MedStack has network-based firewalls enabled and configured for all customer virtual networks and servers.
MedStack has host-based firewalls enabled and configured for all customer virtual networks and servers.
Enabling the “Most strict” option for a load balancer within MedStack enforces the use of strong ciphers for TLS. This is recommended for all applications and PCI DSS compliance.
Leave the technical architecting to us and spend your time doing what you do best. To learn more about how MedStack can help you save months of developer hours, or to learn more about our Security Program, check out our support documentation.
Learn how MedStack can help you.